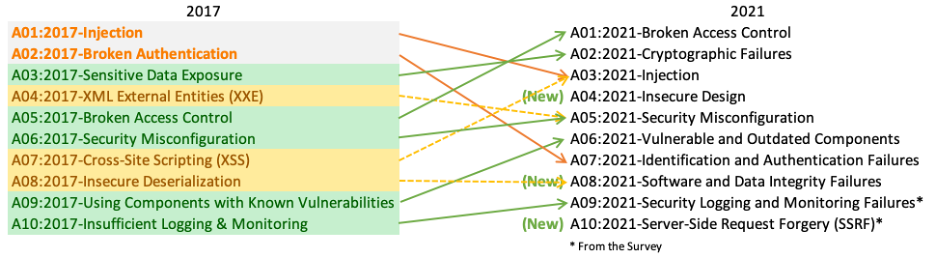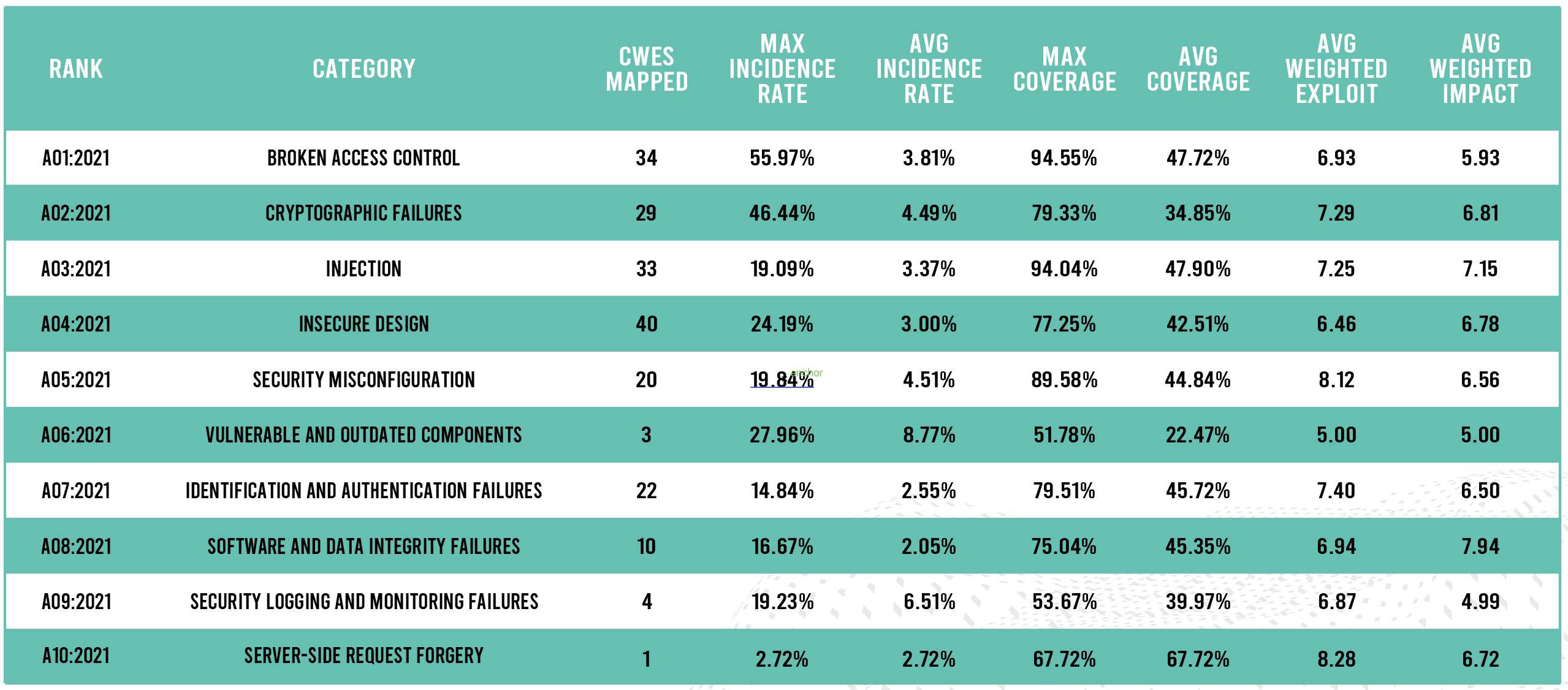
THE 2021 OWASP TOP TEN EMPHASIZES SECURITY CONTROL AREAS OVER INDIVIDUAL VULNERABILITIES FOR IMPROVED RISK MANAGEMENT - Security Boulevard

PDF) AN ASSIGNMENT ON OWASP top 10 Security threat and map with top 10 proactive controls to mitigate the risk of web application
OWASP Top 10 Proactive Controls IEEE Top 10 Software Security Design Flaws OWASP Top 10 Vulnerabilities Mitigated OWASP Mobile T